-

Two Decades of Trusted Partnership: Empowering Your IT Success
We are honored to celebrate 20 years of partnering with valued clients like you. Since our founding in 2003, we have established a legacy of delivering industry-leading IT solutions and services. Throughout this journey, our unwavering focus has remained on fostering strong client relationships and empowering your success in the ever-evolving technological landscape. Our commitment…
-

Reliable IT Solutions for Southeast Wisconsin Businesses
Gartner Technology has been a trusted IT partner for companies throughout Southeast Wisconsin since 2003. We deliver comprehensive technology services and solutions to organizations in Sheboygan, Ozaukee, Fond du Lac, Washington and Calumet Counties. Network Design & ImplementationFrom structured cabling to WiFi deployments, we design and implement secure, high-speed network infrastructure tailored to your requirements.…
-

Web Development Unveiled
The internal workings of web development are like a fascinating, complex engine with many interconnected parts. Let’s dive into the gears and pistons of this digital machine: Front-End: This is the flashy storefront, the part users interact with directly. It’s built using: Back-End: Sometimes referred to as the content repository or administration panel, is the…
-

Who Owns Your Domain Name?
Your domain name is your web address, or the part after the @ in your email address. Our domain is gartnertechnology.com. Who owns your domain name anyway? Sounds like a pretty simple question, doesn’t it? Technically, the question is “Who holds the rights to your domain name?” According to Google: A registrant is the registered…
-

Microsoft 365 Support
This is a message that I received from a support tech at Microsoft after getting a complex issue quickly solved. These folks are very responsive. When initiated through the 365 admin portal, the support response is rarely more than 20 minutes, either by phone call, or email. My choice. Thank you for all your time…
-

A Simple way to Find Your Windows Server 2019 Product Key
Server product keys, like most other OS product keys can typically be found on a label affixed to the chassis of the device in question. Occasionally, we may need access to these product keys when physical access to the device is not practical. For example, I recently needed the product key for a server that…
-
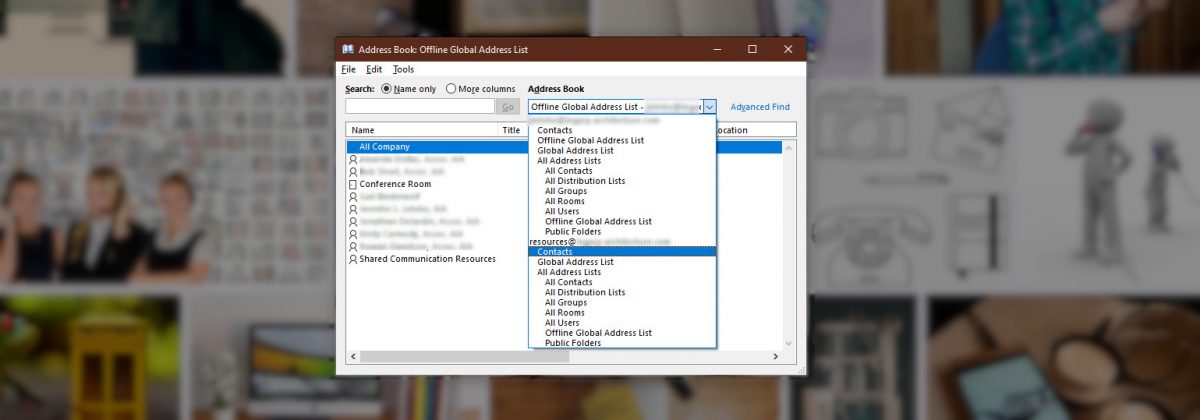
Outlook 365 Shared Contacts in Address Book – Solved
One of our clients wants a company wide contact list through Microsoft 365. It makes sense that this shared contact list would show up in the Outlook Address Book, but apparently, this is not how Outlook works. First, I followed this guide: https://docs.microsoft.com/en-us/outlook/troubleshoot/calendaring/how-to-share-calendar-and-contacts… and the group and calendar show up in Outlook right away, as expected, but…
-
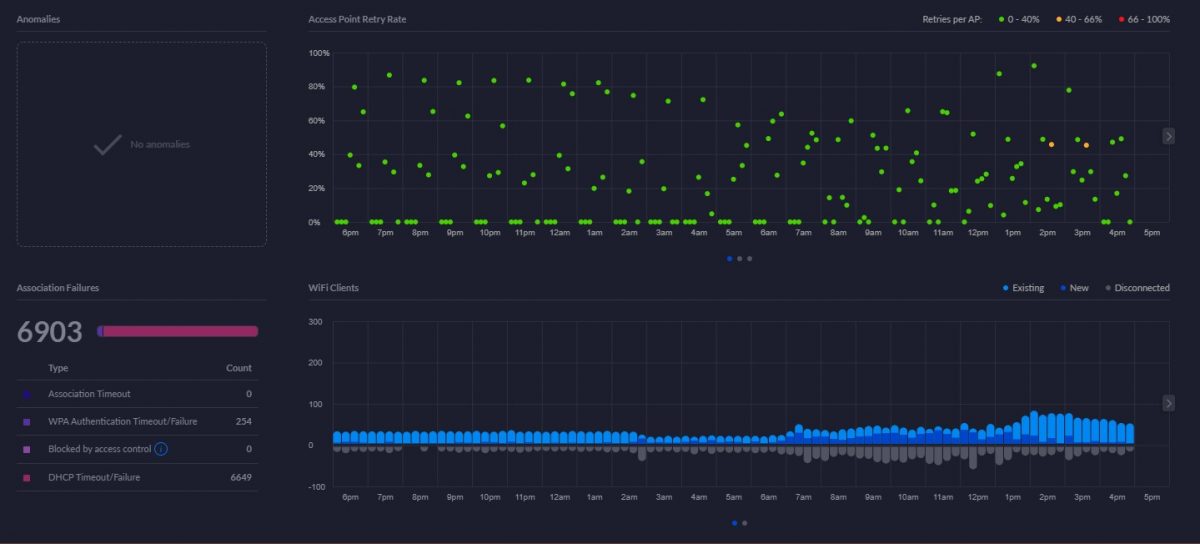
Unifi USG DHCP Timeout/Failure – Solved
I’ve recently had an issue with one of the UniFi installations that I manage. The internet speed was upgraded so I made some optimizations to the network to better utilize the potential increase in bandwidth. Prior to completing my tweaks, all wireless clients suddenly could no longer get an IP address from the USG DHCP…
-

Microsoft Surface Pro 3 Dead Zone Fixed!
We bought a Surface Pro 3 a few years back when it was new. After about 13 months – right after the warranty expired – a dead zone developed on the touch screen in which touch by hand or pen/stylus would not function. This was the approximately top 1/3 of the screen. After much searching…